Cybersecurity
Cybersecurity isn’t just for ‘tech people’ anymore. Here’s why.
Cybersecurity is now the responsibility of everyone in your organization, not just your information technology department.
It takes only one keystroke to set off an organization-wide cybersecurity crisis. Someone clicks on a shared Google Doc, and suddenly screens go black, machines lock up, and sensitive data is destroyed or goes missing.
And the responsibility for the whole fiasco lands squarely on the shoulders of the executive team, many of whom might not have much, if any, of the deep technical background required to address it.
This spring, a new MIT Sloan Executive Education course, “Cybersecurity Leadership for Non-Technical Executives,” will focus on helping leaders have more intelligent conversations with the folks in their organizations who do have that background — their own technical experts. The course will be led by professor Stuart Madnick, a director of Cybersecurity at MIT Sloan, or CAMS, an interdisciplinary consortium dedicated to improving critical infrastructure cybersecurity, alongside CAMS executive director Keri Pearlson and CAMS director Michael Siegel.
"This program is intended to help the participants to take the necessary active leadership role in guiding their organization through the cybersecurity challenges that they must confront and overcome,” said Madnick. "The center is uniquely focused on the managerial, organizational, and strategic aspects of cybersecurity — the critical needs for leaders in our modern enterprises. MIT played a key role in the development on the internet, so it makes sense to come to MIT to learn how to protect your use of the internet.
"There’s a growing need for cybersecurity to be viewed from a holistic perspective, not just as the responsibility of security and technology executives, said Pearlson. Technologists “make great decisions, but they don’t necessarily understand your business. As an executive, you [need to] understand enough to be a knowledgeable participant in those discussions,” Pearlson said.
“That doesn’t mean that everybody in the organization has to understand how the firewall works and what the in-depth defense architecture is, but it does mean that everybody has a responsibility to keep the organization safe and cybersecure,” Pearlson continued. “It only takes one bad actor or one mistake to put the whole organization in jeopardy.”
Getting the people in an organization up to speed with what it takes to prevent cyberattacks is just as important, and arguably more difficult, than getting the right technological measures in place, said Pearlson.
“You have to get people to do things, and organizations to move, and sometimes that’s trickier,” Pearlson said.
But it’s not impossible, and when it works, organizations will find themselves less susceptible to being victimized by cyberthreats, and more resilient when they are. Here’s how to do it.
View the problem holistically
When an organization finds itself on the receiving end of a cyberattack, whether it’s a ransomware attack locking up its computer systems until cryptocurrency is forked over or hackers making off with hundreds of thousands of credit card numbers, the tendency is to put the blame on whoever fell for the bait or left an opening, Madnick said.
But in reality, the fault doesn’t lie with just one person: It has roots deeper in the organization’s cybersecurity culture. “People tend to say ‘Oh, John Jones there or whoever left the back door open,’” Madnick said. “That’s not the problem. It was also that the windows were left open and the key was left under the doormat. People tend to jump on the guy who left the door open, not realizing that everybody’s doing everything wrong. He just happened to be ‘that guy.’”
While most organizations provide their workforce with a sort of “cybersecurity inoculation,” usually in the form of an annual workshop, creating a cybersecure culture requires much more than that, Pearlson said.
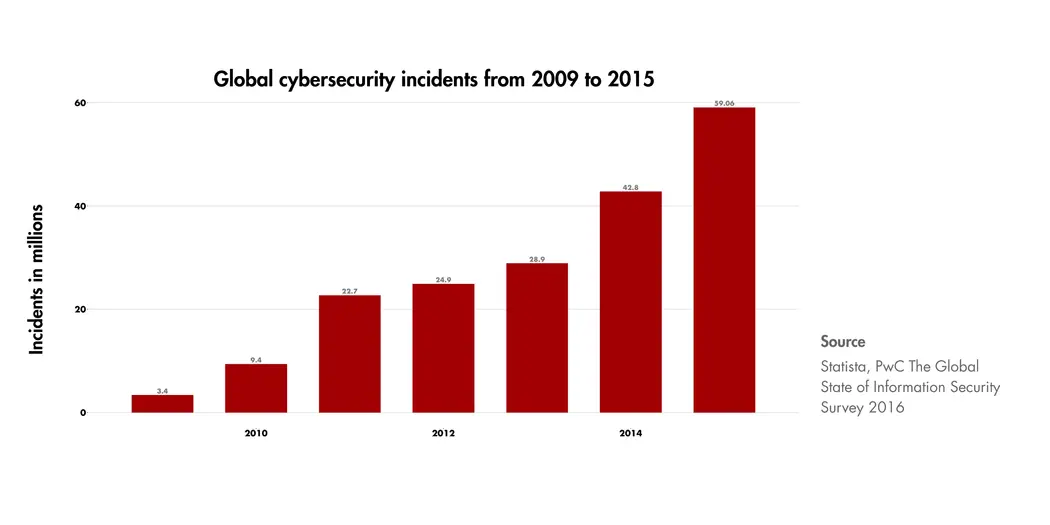
Global cybersecurity incidents have been increasing year over year.
Credit: Tom Relihan
One of the best things leaders can do is make cybersecurity a top priority and invest in it accordingly. That projects its importance out to the rest of the organization. “That sends a different message than an email from the executive desk that just says ‘By the way, don’t forget: We want to be cybersecure,’” Pearlson said.
Identify your ‘crown jewels’ now
Do you know the most critical parts of your organization to protect from cyberattacks — your “crown jewels”? If not, now is the time to figure that out and put protective measures in place, Pearlson said.
“It’d be nice to protect everything, and you have to have layers of protection on everything, but at some point you have to make a decision about what the crown jewels are,” she said. “Then, the other piece is ‘What are the risks of this particular jewel being compromised, and what do I have to do to protect it?’”
Keep a check on connectivity
Is the chiller in one of your laboratories that keeps dangerous substances from exploding connected to the internet? That might be a great convenience if you want to control it remotely, but it’s also a vulnerability. Any device connected to the internet — any piece of the “internet of things” — has the potential to be hacked, Pearlson said, from the lights in your industrial greenhouse to the coffee maker in your break room.
Now is a good time to review which devices are or could be connected to the internet, and to put into place white lists — lists of what connections are acceptable for a device to listen to — and black lists — the connections that are not. All it could take is for a contractor to come plug into the system for service to have a potential problem. Even systems that are “air gapped,” or sequestered from your own network, aren’t completely safe if the contractor connects to it with a compromised system.
Have a plan — and a plan for when that plan fails
No matter how many levels of protection you put in place, there’s always that blind spot where you just couldn’t anticipate an attack. Once your system has been compromised, you have to have response and recovery plans in place.
If the people responsible for shutting down a crucial system during an attack are waiting for a phone call or email from you to execute their duty, what happens when the attack disables both of those avenues? A plan to regroup on a separate system, or on cell phones on a different network dedicated to that purpose, could be the answer. But it pays to have a plan B — and a plan C, because there’s a good chance your plan B might also be compromised.
“You need multiple layers of response. I mean, three, four, or five layers,” Pearlson said. And those response muscles need to be worked out ahead of time in simulations or drills, she stressed. “It’s one of the hardest things for companies to do, because they’re not having a problem right now.”
Understand and monitor the dark web
“The dark web is no longer just a bunch of fringe individuals in hoodies in a dark corner, typing away trying to break into your systems,” Pearlson said. “Those people do exist, but the dark web is actually a very well-organized ecosystem of service providers. You can buy just about any service you want — threat intelligence, payment processing, phishing.”
And once you’re aware of what is available on the dark web, she said, you can start to pull together a picture of where a less ethical person could piece them together into an attack vector and anticipate facing an attack of that sort in the future.
“You’re not waiting for the next attack on your company. Instead, you might be able to see activity around these services and see it forming before it’s actually attacking you or attacking the ecosystem,” Pearlson said. “It’s a different way to think about the dark web.”